Full names Mr/Mrs/Miss
Address
Married/Never married/ Widowed/Divorced/Separated___________
Date of birth_____________________________________________
Nationality_______________Country of birth__________________
Do you or any of your dependendants suffer, or have any of you ever suffered from any physical or mental disability? (Yes or No)_______
If yes, give full details_____________________________________ _______________________________________________________
Number and ages of children over the age of 1,5 years:
| Name | Age | Qualification |
| For official use |
Have you ever resided in the USA, if so,
please give details
Items (A) and (D) must be completed by all applicants
Items (B) and (C) must only be completed if applicable
(A) School education: total number of years From To
Primary school ___________________________________________
Secondary/High school ____________________________________
Professional school _______________________________________
Highest examinations passed ________________________________
Major subjects ___________________________________________
(B) Higher education or special training:
Name of college, university or institution attended _______________ _______________________________________________________
Prescribed duration of course _______________________________
Period attended: From________________to____________________
Major subjects ___________________________________________
What degree, diploma or certificate obtained____________________
(C) Trade qualifications:
Duration of apprenticeship training; from__________to___________
Trade in which qualified____________________________________
(D) Record of employment: (these details must be in date
order including periods of unemployment for the last 20
years)
| Name of firm | City/Town in which located | From To | Nature of work |
(E) Describe briefly your present/last duties ____________________ _______________________________________________________
(F) What is the trade or business of your present/last
employer? _______________________________________________
(G) What is your present/ last monthly salary or income?__________
(H) What occupation do you intend following in USA? ___________
(I) Do you receive a pensio or do you have a private
income? If so, please give details ____________________________
(J) Have you an offer of employment in USA? If so, attach copy of the offer ________________________________________________
(K) Language proficiency: __________________________________
(a) What is your mother tongue? _____________________________
(b) What is your proficiency in other languages? (Answer YES or NO under the different headings)
| Language | Speak | Read | Write |
| English | |||
(L) Details regarding relatives and friends in the USA
| Name | Address | Relationship |
Date _____________________________________________________
ІІІ. Письмово перекладіть всі пункти анкети українською мовою.
Питання для самоконтролю:
1. Are there dirrerent types of questionnaires in every country?
2. When are questionnaires used?
3. To fill in a questionnaire is just a formality, isn`t it?
4. Can a questionnairy influence one`s professional career?
Рекомендована література:
1. Business Writing Clear and Simple Copyright © 2007 Learning Express, LLC.
2.David Chappell, Derek Marshall Vinsent, Power-Smith Simon Cavender. Building Contract Dictionary.Third Edition.
3.John Forster.Effectiv writing skills for Public Relations. Forth Edition.
Дидактичне забезпечення: анкета, українсько-англійський словник.
САМОСТІЙНА РОБОТА №11
Тема: Технічний переклад та переказ тексту за фахом: «Комп`ютерна наука»
Завдання до самостійної роботи:
І. Знайдіть у правій колонці українські еквіваленти англійських слів та словосполучень
| 1. to deal (with) | а. програмне забезпечення |
| 2. to elaborate (to work out) programs | b. відповідати сучасним вимогам |
| 3. computer-aided design | с. апаратна частина |
| 4. computer-aided manufacturing | d. мати справу з(кимось або чимось) |
| 5. to meet up-to-date demands (requirements) | е. автоматизоване проектування |
| 6. software | f. захищати від вірусів |
| 7. hardware | g.пропонувати рішення |
| 8. to offer solutions | h. разробляти програми |
| 9. to solve problems | i. автоматизоване виробництво |
| 10. to defend from viruses | j. вирішувати проблеми |
ІІ. Перекладіть письмово українською мовою слова-інтернаціоналізми, що зустрічаються у тексті:
specialist, productivity, optimal, problem, logic, operation, program, virus, expert, instruction, method, computer, mathematics, designer, manager, calculator.
ІІІ. Прочитайте та письмово пнрекладіть текст українською мовою:
«Computer Science»
Computer science is a part of an applied mathematics. Specialists in computer science say that this field of knowledge is very interesting because it deals with computer-aided-design (CAD) and computer-aided-manufacturing (CAM).
Computers are intended to improve the productivity of labour of scientists, designers, engineers, managers, and other specialists, because computers offer quick and optimal solutions. One of the main goals of using CAD/CAM is to shorten tjje time between designing and manufacturing.
Moreover, computers came in our life and to our houses and now we can solve our everyday problems with their help.
Computers can be divided into simple and complex devices. Simple computers such as calculators can perform addition, subtraction, multiplication and division. As far as complex computers are concerned they can do different logical operations and some of them even have artificial intelligence.
Thus in order to elaborate up-to-date and inexpensive programs as well as to defend them from viruses, it is important to know some programming languages.
There are low-level programming languages such as a machine language and an assembly language and high-level programming languages, for instance, FORTRAN, PASCAL, ADA, C, BASIC, etc.
ІV. Усно перекажіть текст англійською мовою.
Питання для самоконтролю
1. What do specialists in computer science deal with?
2. What are the computers used for?
3. What operations can simple devices perform?
4. What operations do complex computers perform?
5. What are CAD/CAM systems intended to do?
6. What high-level programming languages do you know?
Рекомендована література:
1. Гальперин И.Р., Медникова Э.М. Большой англо-русский политехнический словарь. – Москва: Русский язык, 1987.
2. Федоршин О.П., Євстіфєєв П.Ф., Рябушенко Т.Л. Англійська мова. Практикум з науково-технічного перекладу, – Тернопіль Навчальна книга – Богдан, 2002 – 52с.
3. Чебурашкин Н.Д. Хрестоматия по техническому переводу. – Москва: Просвещение, 1987.
4. Полякова Т.Ю Английский язык для инженеров. Учебник. М.: Bысшая школа, 2003.- 243 с
5. Лоскутова Г.В. О компьютере по-английски. – Санкт-Питербург: КАРО. – 2004
6. IBM PC для пользователя. – Краткий курс. – М.: ИНФА. – 1999
Дидактичне забезпечення: текст, словник.
САМОСТІЙНА РОБОТА №12
Тема: Технічний переклад та переказ тексту за фахом: «Інтернет»
Завдання до самостійної роботи:
І. Усно перекладіть текст. Перекладіть українською мовою письмово 1-й і 4-й абзаци.
«The Internet»
1. The Internet, a global computer network which embraces millions of users all over the world, began in the United States in 1969 as military experiment. It was designed to survive a nuclear war. Information sent over the Internet takes a shortest path available from one computer to another. Because of this, any two computers on the Internet will be able to stay in touch with each other as long as there is a single route between them. This technology is called packet switching. Owning to this technology, if some computers on the network are knocked out (by nuclear explosion, for example), information will just rout around them. One such packet-switching network already survived a war. It was the Iraqi computer network, which was not knocked out the Gulf War.
2. Most of the Internet computers (more then 50%) are in the United States, while the rest located in more than 100 other countries. Although the number of host computers can be counted fairy accurately, nobody knows exactly how many people use the internet, there are millions, and their number is growing by thousands each month worldwide.
3. The most popular Internet service is e-mail. Most of people, who have access to the Internet, use the network only for sending and receiving e-mail messages. However, other popular services are available on the Internet: reading USENET News, using the World-Wide Web, telnet, FTP and Gopher.
4. In many developing countries the Internet may provide businessmen with a reliable alternative to the expensive and unreliable telecommunications systems of these countries. Commercial users can communicate over the Internet with the rest of the world and do it very cheaply. When they send e-mail messages, they only pay for phone calls to their local services provider, not for calls across their countries or around the world. But who actually pays for sending e-mail messages over the Internet long distances, around the world? The answer is very simple: a user pays his\her service provider a monthly or hourly fee. Part of this goes towards its costs to connect to a larger service provider. And part of the fee got by larger provider goes to cover its cost of running a worldwide network of wires or wireless stations.
ІІ. Передивіться текст ще раз і дайте відповіді на такі запитання усно.
· What can Internet provide its users with?
· What do users have to pay for?
· Where are the Internet host computers located?
ІІІ. Знайдіть у тексті англійські еквіваленти іменників. Укажіть дієслова того ж кореня, заповнивши табличку:
| ІМЕННИК | ДІЄСЛОВО | ||
| слово | переклад | слово | переклад |
| a help | допомога | to help | допомогати |
| користувач | |||
| ціна, вартість | |||
| постачальник послуг | |||
| повідомлення, відомість | |||
| доторк, контакт | |||
| служба, обслуговування |
Питання для самоконтролю:
1. Does a global computer network embrace hundreds of users all over the world?
2. Did the Internet, begin in the United States or in Great Britain?
3. What the military experiment in 1969 resulted for?
4. What is the most popular Internet service?
5. Why do businessmen prefer the Internet to the telecommunications systems of there countries?
6. What do we pay for, when sending e-mail messages?
7. Who pays for sending e-mail messages over the Internet long distances, around the world?
Рекомендована література:
1. IBM PC для пользователя. – Краткий курс. – М.: ИНФА. – 1999
2. Гальперин И.Р., Медникова Э.М. Большой англо-русский политехнический словарь. – Москва: Русский язык, 1987.
3. Лоскутова Г.В. О компьютере по-английски. – Санкт-Питербург: КАРО. – 2004
4. Федоршин О.П., Євстіфєєв П.Ф., Рябушенко Т.Л.Англійська мова. Практикум з науково-технічного перекладу, – Тернопіль Навчальна книга – Богдан, 2002 – 52с.
5. Чебурашкин Н.Д. Хрестоматия по техническому переводу. – Москва: Просвещение, 1987.
Дидактичне забезпечення: текст, словник.
САМОСТІЙНА РОБОТА №13
Тема: Технічний переклад та переказ тексту за фахом: «Класифікація комп’ютерних мереж»
Завдання до самостійної роботи:
І. Усно перекладіть текст. Перекладіть українською мовою письмово абзаци “Peer-to-Peer”, “Client – Server”.
«Computer network classification»
A computer network is a system for communication among two or more computers. Computer networks can be categorized by range, functional relationship, network topology and specialized function.
A computer network, often simply referred to as a network, is a collection of hardware components and computers interconnected by communication channels that allow sharing of resources and information. Where at least one process in one device is able to send/receive data to/from at least one process residing in a remote device, then the two devices are said to be in a network.
Networks may be classified according to a wide variety of characteristics such as the medium used to transport the data, communications protocol used, scale, topology, and organizational scope.
Peer-to-Peer
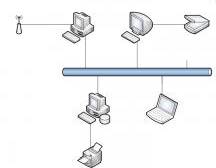 The first type of network that we will consider is called peer-to-peer. In a peer-to-peer network, network hosts don't have a specific role. They provide network services and they also consume network services. In a peer-to-peer network we can have hosts that will fulfill a variety of different roles. For example, one computer can have a printer connected to it which is shared on the network. Another computer can have a large hard drive installed and everyone is allowed to put files on that hard drive. So, in this situation we have hosts that both provide and consume network services. In essence, they function both as a client and as a server at the same time. The main benefit of peer-to-peer network is the ease of installation. All we have to do is share our resources on the network. It's also very inexpensive. Of course, there's some drawbacks to a peer-to-peer network. First of all, a peer-to-peer network is not very scalable which means that the bigger it gets, the harder it is to manage it. That's because they lack centralized control.
The first type of network that we will consider is called peer-to-peer. In a peer-to-peer network, network hosts don't have a specific role. They provide network services and they also consume network services. In a peer-to-peer network we can have hosts that will fulfill a variety of different roles. For example, one computer can have a printer connected to it which is shared on the network. Another computer can have a large hard drive installed and everyone is allowed to put files on that hard drive. So, in this situation we have hosts that both provide and consume network services. In essence, they function both as a client and as a server at the same time. The main benefit of peer-to-peer network is the ease of installation. All we have to do is share our resources on the network. It's also very inexpensive. Of course, there's some drawbacks to a peer-to-peer network. First of all, a peer-to-peer network is not very scalable which means that the bigger it gets, the harder it is to manage it. That's because they lack centralized control.
Client – Server
Another classification within the host roles category is a client server network. In a client server network, unlike a peer-to-peer network, network hosts have specific roles assigned to them. We have certain systems, certain hosts that are assigned to be servers. A server provides network resources. On a client server network we also have clients. A client does not provide network services, it only consumes network services. Clients will not have have, for instance, shared storage or printers. All those services are provided by the server. Server provides the resources, the client simply use the resources. With a peer-to-peer network everybody had the same operating system, but in a client server network client workstations have generic operating systems that provide functionality. For example, clients could have Windows XP or Windows 2000 installed. Servers would have some special optimized operating system like Server 2003. These operating systems are designed to provide these network resources and are not designed for client type tasks. The main benefit of this type of network is that it's very highly scalable. That means it's very easy to expand the size of the network, it's very easy to add more clients and it's very easy to add more servers. Client server networks are also much easier to support. That's because services are centralized. If we know where are all the services, we know where to look when we have some problems with them. Backup is also a lot easier. We can configure that users store their data on the server. That way, instead of having to back up individual workstations we only need to backup one location - the server. There are some drawbacks. Operating systems for servers are fairly expensive (the exception, of course, is Linux). The other thing is that this type of network takes a lot of planning. We have to decide which servers are going to host which services, where they're going to be placed on the network, etcetera.
ІІ. Передивіться текст ще раз і складіть до нього 10 питань різних типів.
ІІІ. Знайдіть у тексті англійські еквіваленти іменників. Укажіть дієслова того ж кореня, заповнивши табличку:
| ІМЕННИК | ДІЄСЛОВО | ||
| слово | переклад | слово | переклад |
| a category | категорія | to categorize | класифікувати, розбити по категоріям |
| сервер | |||
| процесор | |||
| програма | |||
| план | |||
| будівля |
Питання для самоконтролю:
8. What does the term “Computer network” wean?
9. Does a global computer network embrace hundreds of users all over the world?
10. What Computer network classification do you know?
Рекомендована література:
6. IBM PC для пользователя. – Краткий курс. – М.: ИНФА. – 1999
7. Гальперин И.Р., Медникова Э.М. Большой англо-русский политехнический словарь. – Москва: Русский язык, 1987.
8. Лоскутова Г.В. О компьютере по-английски. – Санкт-Питербург: КАРО. – 2004
9. Федоршин О.П., Євстіфєєв П.Ф., Рябушенко Т.Л.Англійська мова. Практикум з науково-технічного перекладу, – Тернопіль Навчальна книга – Богдан, 2002 – 52с.
10. Чебурашкин Н.Д. Хрестоматия по техническому переводу. – Москва: Просвещение, 1987.
Дидактичне забезпечення: текст, словник.
САМОСТІЙНА РОБОТА №14
Тема: Технічний переклад та переказ тексту за фахом: «Міська комп’ютерна мережа»
Завдання до самостійної роботи:
I. Скласти словник незнайомих слів з тексту (не менше 10 слів).
Наприклад:
| Слово | Транскрипція | Переклад |
| distribution | [,distri`bju∫n] | розподіл |
II. Вивчити слова на пам'ять
III. Усно перекласти текст українською мовою. Перекласти абзаци № 1, 2, 4 тексту письмово українською мовою
IV. Скласти анотацію англійською мовою (письмово)
V. Переказати текст згідно анотації.
«Metropolitan area network»
1. A metropolitan area network (MAN) is a computer network that usually spans a city or a large campus. A MAN usually interconnects a number of local area networks (LANs) using a high-capacity backbone technology, such as fiber-optical links, and provides up-link services to wide area networks (or WAN) and the Internet.
2. The IEEE 802-2002 standard describes a MAN as being[1]:“ A MAN is optimized for a larger geographical area than a LAN, ranging from several blocks of buildings to entire cities. MANs can also depend on communications channels of moderate-to-high data rates. A MAN might be owned and operated by a single organization, but it usually will be used by many individuals and organizations. MANs might also be owned and operated as public utilities. They will often provide means for internetworking of local networks.”
3. Authors Kenneth C. Laudon and Jane P. Laudon (2001) of Management Information Systems: Managing the Digital Firm 10th ed. define a metropolitan area network as:“ A Metropolitan Area Network (MAN) is a large computer network that spans a metropolitan area or campus. Its geographic scope falls between a WAN and LAN. MANs provide Internet connectivity for LANs in a metropolitan region, and connect them to wider area networks like the Internet” It can also be used in cable television.
Implementation
4. Some technologies used for this purpose are Asynchronous Transfer Mode (ATM), FDDI, and SMDS. These technologies are in the process of being displaced by Ethernet-based connections (e.g., Metro Ethernet) in most areas. MAN links between local area networks have been built without cables using either microwave, radio, or infra-red laser links. Most companies rent or lease circuits from common carriers because laying long stretches of cable can be expensive.
5. DQDB, Distributed-queue dual-bus, is the metropolitan area network standard for data communication. It is specified in the IEEE 802.6 standard. Using DQDB, networks can be up to 20 miles (30 km) long and operate at speeds of 34 to 155 Mbit/s.
6. Several notable networks started as MANs, such as the Internet peering points MAE-West, MAE-East, and the Sohonet media
Питання для самоконтролю:
1. What is MAN?
2. What technologies are used for MAN?
Рекомендована література:
11. IBM PC для пользователя. – Краткий курс. – М.: ИНФА. – 1999
12. Гальперин И.Р., Медникова Э.М. Большой англо-русский политехнический словарь. – Москва: Русский язык, 1987.
13. Лоскутова Г.В. О компьютере по-английски. – Санкт-Питербург: КАРО. – 2004
14. Федоршин О.П., Євстіфєєв П.Ф., Рябушенко Т.Л.Англійська мова. Практикум з науково-технічного перекладу, – Тернопіль Навчальна книга – Богдан, 2002 – 52с.
15. Чебурашкин Н.Д. Хрестоматия по техническому переводу. – Москва: Просвещение, 1987.
Дидактичне забезпечення: текст, словники.
САМОСТІЙНА РОБОТА №15
Тема: Технічний переклад та переказ тексту за фахом: “Security and safety standard ”
Завдання до самостійної роботи:
1. Скласти словник незнайомих слів з тексту (не менше 10).
Наприклад:
| Слово | Транскрипція | Переклад |
| security | [sə`kjurəti] | безпека |
2. Вивчити слова на пам'ять
3. Перекласти текст усно українською мовою.
Перекласти “ 9 Steps to Protecting Your Computer from Viruses and Other Malware ” письмово українською мовою
4. Скласти анотацію англійською мовою (письмово)
5. Переказати текст згідно анотації.
“Security and safety standard”
9 Steps to Protecting Your Computer from Viruses and Other Malware
Achieving good computer security can seem like a daunting task. Fortunately, following the few simple steps outlined below can provide a good measure of security in very little time.
1) Use antivirus software and keep it up-to-date. You should check for new definition updates daily. Most antivirus software can be configured to do this automatically.
2) Install security patches. Vulnerabilities in software are constantly being discovered and they don't discriminate by vendor or platform. It's not simply a matter of updating Windows; at least monthly, check for and apply updates for all software you use.
3) Use a firewall. No Internet connection is safe without one. Firewalls are necessary even if you have a dial-up Internet connection -- it takes only minutes for a a non-firewalled computer to be infected.
4) Secure your browser. Many labor under the dangerous misconception that only Internet Explorer is a problem. It's not the browser you need to be concerned about. Nor is it a matter of simply avoiding certain 'types' of sites. Known, legitimate websites are frequently being compromised and implanted with malicious javascript that foists malware onto visitors' computers. To ensure optimum browsing safety, the best tip is to disable javascript for all but the most essential of sites -- such as your banking or regular ecommerce sites. Not only will you enjoy safer browsing, you'll be able to eliminate unwanted pop-ups as well.
5) Take control of your email. Avoid opening email attachments received unexpectedly -- no matter who appears to have sent it. Remember that most worms and trojan-laden spam try to spoof the sender's name. And make sure your email client isn't leaving you open to infection. Reading email in plain text offers important security benefits that more than offset the loss of pretty colored fonts.
6) Treat IM suspiciously. Instant Messaging is a frequent target of worms and trojans. Treat it just as you would email.
7) Avoid P2P and distributed filesharing. Torrent, Kazaa, Gnutella, Morpheus and at least a dozen other filesharing networks exist. Most are free. And all are rife with trojans, viruses, worms, adware, spyware, and every other form of malicious code imaginable. There's no such thing as safe anonymous filesharing. Avoid it like the plague.
8) Keep abreast of Internet scams. Criminals think of clever ways to separate you from your hard earned cash. Don't get fooled by emails telling sad stories, or making unsolicited job offers, or promising lotto winnings. Likewise, beware of email masquerading as a security concern from your bank or other eCommerce site.
9) Don't fall victim to virus hoaxes. Dire-sounding email spreading fear, uncertainty and doubt about non-existent threats serve only to spread needless alarm and may even cause you to delete perfectly legitimate files in response.
Remember, there's far more good than bad on the Internet. The goal isn't to be paranoid. The goal is to be cautious, aware, and even suspicious. By following the tips above and becoming actively engaged in your own security, you'll not only be protecting yourself, you'll be contributing to the protection and betterment of the Internet as a whole.
Crime Prevention
Every business owner, manager and employee plays a part in making businesses safe. Here are some things you can do to help prevent robbery:
- Have at least two employees open and close the business.
- Do not release personal information to strangers.
- Keep purses and personal valuables locked in desks or lockers.
- Install a robbery alarm.
- Place a surveillance camera behind the cash register facing the front counter. Replace videotapes regularly.
- Vary times and routes of travel for bank deposits.
- Don't use marked "moneybags" that make it obvious to would-be robbers you are carrying money for deposit.
- Keep a low balance in the cash register.
- Place excess money in a safe or deposit it as soon as possible.
- Cooperate with the robber for your own safety and the safety of others. Comply with a robber's demands. Remain calm and think clearly. Make mental notes of the robber's physical description and other observations important to law enforcement officers.
- If you have a silent alarm and can reach it without being noticed, use it. Otherwise, wait until the robber leaves.
- Be careful, most robbers are just as nervous as you are.
- Keep your business neat and clean. A tidy, orderly place of business is inviting to customers, but not to robbers. Dressing neatly also sends the right message.
- Stay alert! Know who is in your business and where they are. Watch for people who hang around without buying anything. Also, be aware of suspicious activity outside your place of business. Write down license numbers of suspicious vehicles if visible from the inside of your business.
- Make sure the sales counter can be seen clearly. Don't put up advertisements, flyers, displays, signs, posters or other items on windows or doors that might obstruct the view of the register from inside or outside your business. The police cruising by your store need to see in.
- Try to greet customers as they enter your business. Look them in the eye, and ask them if they need help. Your attention can discourage a robber.
- Keep your business well-lit, inside and outside. Employees should report any burned-out lights to the business owner or manager. Keep trees and bushes trimmed, so they don't block any outdoor lights.
- Encourage the police to stop by your business.
- Learn the names of the officers who patrol your business.
- Use care after dark. Be cautious when cleaning the parking lot or taking out the trash at night. Make sure another employee inside the business keeps you within eye contact while you are involved in work details outside of your building.
- If you see something suspicious, call the police. Never try to handle it yourself. It could cost you your life.
- Handle cash carefully. Avoid making your business a tempting target for robbers. Keep the amount of cash in registers low. Drop all large bills right away. If a customer tries to pay with a large bill, politely ask if he or she has a smaller one. Explain that you keep very little cash on hand.
- Use only one register at night. Leave other registers empty and open. Tilt the register drawer to show there is no money in it.
- Leave blinds and drapes partially open during closing hours.
- Make sure important signs stay posted. For example, the front door should bear signs that say, "Clerk Cannot Open the Time Lock Safe."
- If your business is robbed put your safety first. Your personal safety is more important than money or merchandise.
- Don't talk except to answer the robber's questions.
- Don't stare directly at the robber.
- Prevent surprises, keep your hands in sight at all times.
- Don't make any sudden moves.
- Tell the robber if someone is coming out of the back room or vault or working in another area of your business.
- Don't chase or follow the robber out of your place of business.
- Leave the job of catching the robber to the police.
Питання для самоконтролю:
1. Is your computer connected to the Internet?
2. When does a PC become a target for criminals want to access your personal information and use it for their own purposes?
3. How safe is your computer?
4. Do you have anti-virus software installed on your computer to block email virus and worms?
5. Does your anti-virus software automatically update itself with current virus definitions?
6. Do you have a policy of never opening an email attachment even if it is from someone you know?
Рекомендована література:
1. Гальперин И.Р., Медникова Э.М. Большой англо-русский политехнический словарь. – Москва: Русский язык, 1987.
2. Федоршин О.П., Євстіфєєв П.Ф., Рябушенко Т.Л.Англійська мова. Практикум з науково-технічного перекладу, – Тернопіль Навчальна книга – Богдан, 2002 – 52с.
3. Чебурашкин Н.Д. Хрестоматия по техническому переводу. – Москва: Просвещение, 1987.
Дидактичне забезпечення: текст, словник.
САМОСТІЙНА РОБОТА №16
Тема: Складання тез доповіді захисту курсового проекту англійською та українською мовами
Завдання до самостійної роботи:
I. Записати словник слів та висловів (з транскрипцією)
1. course project - курсовий проект
2. diploma project - дипломний проект
3. to present the project - представляти проект
4. in the present course project is shown - в даному курсовому проекті розглядається …
5. the main aim of my course project is - головна ціль мого курсового проекту…
6. the process of course designing is contained of the following sections (parts) - процес курсового проекту має наступні розділи …
7. the first part is … - перший розділ …
8. the economical part - економічний розділ
9. the explanatory note - пояснювальна записка
10. the report is over - доклад закінчено
II. Вивчити слова та вислови напам'ять.
III. Виконати лексично-граматичні вправи до теми:
- Translate the words into English:
Динамічний, технологічний, економічний, графічний, третій розділ, доклад закінчено, пояснювальна записка, технічна частина, розрахунок, процес дипломного (курсового) проектування, дякую за увагу.
- Translate the sentences into English language:
1. Для дипломного проектування було отримано ряд завдань.
2. Перший розрахунковий розділ був динамічний.
3. Одним з головних завдань мого курсового проекту було створити зручний інтерфес для користувача.
4. В доповнення можу сказати наступне...
- Translate the phrases into Ukrainian:
To provide required level of system`s protection, to make datebase, to save time, to improve the employee work efficiency, the programme doesn`t require pre-installation, the theme of my course project is actual at present, the aim of economic part is…, to display selected information in a form of graphics, the purpose of this diploma project creation is….
IV. Скласти тези доповіді захисту курсового проекту англійською та українською мовами за планом:
· presentation;
· the theme;
· the main aim;
· the tasks;
· the sections;
· the conclusion.
V. Оформіть тези доповіді захисту вашого курсового проекту англійською та українською мовами за зразком:
| ТЕЗИ ДОПОВІДІ ЗАХИСТУ КУРСОВОГО ПРОЕКТУ АНГЛІЙСЬКОЮ МОВОЮ | |
| До вашої уваги пропонується курсовий проект на тему… Актуальність теми проекту обумовлена… Метою мого курсового проекту є…. Мною було отримано завдання…. Програма розроблена з метою… Розробка програми виконувалася у середовищі… Висновки У результаті роботи над курсовим проектом було - створено… - розроблено… - розраховано… - відображено… - здобуто досвід роботи з програмою… | (англійський варіант) |
Питання для самоконтролю:
1. How many parts does your course project consist of?
2. What is the main aim of your course project?
3. Are you going to continue to study in ONPU and get high education?
Рекомендована література:
1. Бабайкова І.М., Балацька Л.П., Барабаш О.В. Спілкуємося англійською мовою. Підручник.– Львів: Видавництво «Бескид Біт», 2008.–252c.
2. Мисик Л., Арцишевська А., Кузнєцова Л. Англійська мова. Комунікативний аспект: Підручник для студентів вищих навчальних закладів/ За ред. Л.Мисик – Львів: Cвіт, 2007.–432c.
Дидактичне забезпечення: тези доповіді курсового проекту українською мовою, словники.






