| as... as as many... as as much... as the same... as similar to the same | are similar equal to is like similar/ly equal/ly compared to/with | each either all both alike |
Examples:
1 Here, the term 'processor' is equivalent to the central processing unit.
2 Laptops are as powerful as microcomputers.
3 Some companies have as many computers as employees.
4 Some companies use both disks and conventional filing systems for storing data.
5 A computer virus is like a virus in the human body. It can do a lot of damage.
6 Many word-processing programs are similar in that thother,re certain common functions.
2 Non-equivalence: the following words and constructions are used to compare or contrast things or people that are separate from each other.
| not as... as...-er than more... than fewer... than less... than | greater than not as many... as not as much... as not equal to | unequal(ly) unlike not the same as not all |
Examples:
1 A mainframe is larger and more expensive than a microcomputer.
2 Learning to use a computer is not as difficult as learning to program.
3 A fax board costs less tha(s uperlative),e.
4 Unlike factory-sealed software, pirated versions may contain viruses.
5 Desktop publishing is the same as electronic publishing.
6 You can save money with a network because you will need fewer printers.
3 The highest degree: the following words and constructions are used to compare one member of a group with the whole group (superlative).
the...-est the most... the least...
Examples:
1 This is the most popular package on the market today.
2 BASIC is probably the least difficult programming language to learn.
3 The best programs are those adapted specifically to your own needs.

 4 Parallel increase: the following words and constructions are used to show parallel increase (two comparatives).
4 Parallel increase: the following words and constructions are used to show parallel increase (two comparatives).
the...-er, the more... the more..., the...-er the...-er, the less...
Examples:
1 The more memory your computer has, the more data it can store.
2 The bigger your computer system, the less time you spend waiting.
3 The more training you give to your employees, the better they will perform.
 |
| Exercise 1 | The following sentences express computer capabilities and limitations. Decide whether the sentences express equivalence, non-equivalence, or the superlative, then underline the words expressing the comparison. The first one has been done for you. 1 equivalence Speeds for performing decision-making operations are comparable to those for arithmetic operations. 2 Even the most sophisticated computer, no matter how good it is, must be told what to do. 3 A computer can perform similar operations thousands of times, without becoming bored, tired, or careless. 4 For example, modern computers can solve certain classes of arithmetic problems millions of times faster than a skilled mathematician. 5 _______ One of the most important reasons why computers are used so widely today is that almost every big problem can be solved by solving a number of little problems. 6 Finally, a computer, unlike a human being, has no intuition. |
 |
| Exercise 2 | Read the following sentences taken from previous units. Decide whether the sentences express equivalence, non-equivalence, or the superlative, then underline the words expressing the comparison. 1 Digital Research have continued to develop their operating system, DR/DOS, and it is considered by many people to be a better product than Microsoft's. (Unit 1) 2 For the last generation, Silicon Valley and Tokyo have been working to design computers that are ever easier to use. (Unit 2) 3 There is one thing, however, that has prevented the machines from becoming their user-friendliest:... (Unit 2) 4 Clipboard PCs — which, as their name suggests, are not much bigger than an actual clipboard — replace the keyboard with a liquid crystal display (LCD) screen and an electronic stylus. (Unit 2) 5 When the computer finds the closest match, it encodes the character in memory and displays it on the screen as if it had been typed. (Unit 2) 6 There are a handful of clipboard computers now on the market, including GRIDPad, which is sold in the US; Penvision, manufactured by NCR and sold around the world; and Sony's Palmtop and Canon's Al Note, both sold only in Japan. (Unit 2) 7 I'm frequently asked which online service is 'best' but, the answer is, there is no best. (Unit 3) |
 8 They tend to judge all other online services based on this first service — often preventing themselves from seeing the advantages of a specific service. (Unit 3)
8 They tend to judge all other online services based on this first service — often preventing themselves from seeing the advantages of a specific service. (Unit 3)
9 Each offers one or more products or features that either do not exist elsewhere or are superior to the same features on other services. (Unit 3)
10 Judge it based on what it offers and how it meets your needs —not in comparison to what you're used to using. (Unit 3)
| Exercise 3 | Refer back to the table of word-processing packages (Unit 5, page 58) and write ten sentences comparing the products advertised. Examples: Upword is more expensive than JustWrite. Ami Pro 2.0 has the largest spell check dictionary. |


`There! That should make life easier!'
Start-up
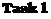 Try to answer these questions.
Try to answer these questions.
1 What is a LAN?
2 What is a WAN?
3 What is a distributed system?

 the text opposite, match these words and phrases with their
the text opposite, match these words and phrases with their
a analyse the syntax of a string of input symbols
b a teleconferencing system allowing users to read messages left by other users
c agreement governing the procedures used to exchange information between co-operating computers
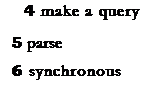 d means of communication between a human user and a computer system
d means of communication between a human user and a computer system
e taking place at exactly the same time as something else
f request a search
 Read quickly through the text below, then match each paragraph with the appropriate summary.
Read quickly through the text below, then match each paragraph with the appropriate summary.
 Network uses, past and present
Network uses, past and present
How distributed systems work
Networks and the future
What networks are and how they operate n The growth of networks, past and present
Computer networks
| C |
omputer networks link computers by communication lines and

 software protocols, allowing data
software protocols, allowing data
5 to be exchanged rapidly and reliably. Traditionally, networks have been split between wide area networks (WANs) and local area networks (LANs). A WAN is a
io network connected over long-distance telephone lines, and a LAN is a localized network usually in one building or a group of buildings close together. The
15 distinction, however, is becoming blurred. It is now possible to connect up LANs remotely over telephone links so that they look as though they are a single LAN.
20 Originally, networks were used
to provide terminal access to another computer and to transfer files between computers. Today, networks carry e-mail, provide
25 access to public databases and bulletin boards, and are
beginning to be used for distributed systems. Networks also allow users in one locality to
30 share expensive resources, such
as printers and disk-systems.
Distributed computer systems are built using networked computers that co-operate to
35 perform tasks. In this environment each part of the networked system does what it is
best at. The high-quality bit-mapped graphics screen of a
40 personal computer or workstation
provides a good user interface.
The mainframe, on the other hand, can handle large numbers of queries and return the results
45 to the users. In a distributed environment, a user might use his
PC to make a query against a

 Computer networks link computers locally or by external communication lines and software allowing data to be exchanged rapidly and
Computer networks link computers locally or by external communication lines and software allowing data to be exchanged rapidly and
reliably. The 2 between local area and wide area networks is,
however, becoming unclear. Networks are being used to perform increasingly diverse tasks, such as carrying e-mail, providing access to public databases,
and for 3. Networks also allow users in one locality to share
resources.
Distributed systems use networked computers. PCs or 4 _
provide the user. Mainframes process 6
and return the results to the users. A user at his PC might make a query against a central database. The PC passes the query, written in a special language, to the mainframe, which then' the query,
returning to the user only the data requested. This allows both the network and the individual PC to operate efficiently.
In the 1980s, at least 100,000 8 were set up world-wide. As
orbit satellites have lowered the price of long-distance telephone calls, data can be transmitted more cheaply. In addition,
10 cable has been installed on a large scale, enabling vast
amounts of data to be transmitted at a very high speed using light signals. This will considerably reduce the price of network access, making global networks more and more a part of our professional and personal lives. Networks should
also improve our work!' and technical abilities.
distinction fibre-optic protocols synchronous
distributed systems LANs queries workstations
environments parses screen handling
| Task 5 Task 6 | Using the line references given, look back in the text and find words that have a similar meaning to: 1 unclear (lines 15-20 2place (lines 25-30) 3 carry out (lines 35-40) 4cost (lines 70-75) 5world-wide (lines 80-85) Now look back in the text and find words that have an opposite meaning to: 1 disparate (lines 10-15) 2conflict v (lines 30-35) 3 preventing (lines 70-75) 4tiny (lines 75-80) 5increase (lines 80-85) |
 Writing
Writing
 Task 7 Translate the third paragraph, beginning 'Distributed computer systems...' into
Task 7 Translate the third paragraph, beginning 'Distributed computer systems...' into
your own language.
Listening

Listen to this extract from the radio programme Computerworks about LANs. Indicate whether the following items are mentioned (✓) or not mentioned (x).
1 LANs are equally useful to large and small companies.
2 ___ Companies can install their own LANs, provided they are not too big.
3 ____ Whether or not a company builds a 'do-it-yourself' LAN depends on the
amount of space available for the installation.
4 It is sometimes still possible to install part of a LAN if you don't have the
computer knowledge or time to do the whole job yourself.
5 _____ You need at least three years' computer maintenance experience before
you should attempt to install a LAN.
6 ____ In order to install your own LAN, you need to be used to opening up
computers, adding and removing expansion boards, and consulting computer documentation.
7 _____ When installing your own LAN you should expect to have to repeat the
same process several times.
8 ____ The installation process often causes computers to break down.

| Task 9 | Read this extract from the tapescript and try to fill in each gap with an appropriate word. When you're installing a LAN, you may be __ your computers for as much as a day or so. A lot depends on how 2 the installation proceeds, and that depends on your own. Professional installers can have each of your machines 4 of _ for only a few minutes at a time. If you can't live without your computers for a while, you |
might want to 6 doing it yourself.
Installing a LAN involves running cable to several'. This may
require you to install junction boxes in walls, do the wiring, and maybe install electrical as well. If you aren't 9 with these skills,
and if you aren't a 1° _ electrician, you will need to hire someone for
this part, at least. Of course, if you're installing your LAN in one room, then you might not need to hire 11
Now listen again to the last part of the recording. Check to see whether your answers match those used by the speaker.
Network configurations
Reading
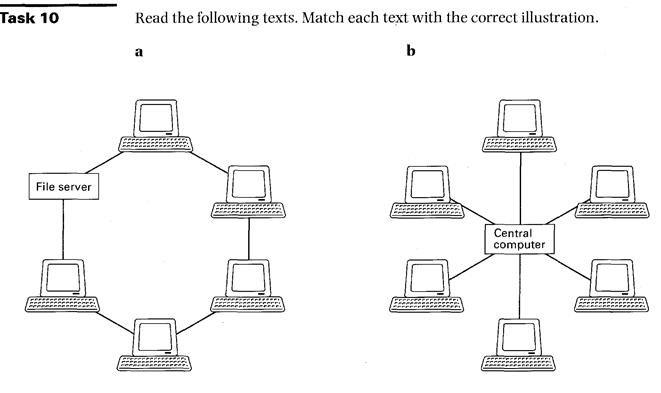
 1 Star
1 Star
In the star configuration, the central computer performs all processing and control functions. All access devices are linked directly to the central computer. The star configuration has two major limitations. First of all, the remote devices are unable to communicate directly. Instead, they must communicate via the central computer only. Secondly, the star network is very susceptible to failure, either in the central computer or the transmission links.
Switched
The central switch, which could be a telephone exchange, is used to connect different devices on the network directly. Once the link is established, the two devices communicate as though they were directly linked without interference from any other device. At the end of the session, the connection is closed, freeing capacity for other users and allowing access to other devices. Multiple switches can be used to create alternative transmission routes.
Ring
Each device is attached to a network shaped as a continuous loop. Data proceeds in only one direction and at a constant speed round the loop. Devices may send information only when they are in control of the 'token'. The token is a package of data which indicates which device has control. The receiving device picks up the token, then clears it for another's use once it has received the message. Only one device may send data at any given moment,
and each device must be working for the network to function.
Bus/Ethernet
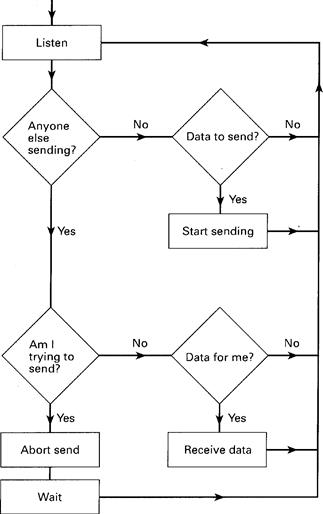
A bus network consists of one piece of cable terminated at each end to which all devices are connected. In a bus-based network, each device is able to broadcast a message when it has detected silence for a fixed period of time. All devices receive the broadcast and determine from the content of the message whether it was intended for them. The only problem occurs when two devices try to send at the same time. When a sending device detects another's transmission, it aborts its own.
Task 11 These are answers to questions about the texts. Write the questions.
1 To connect different devices on the network directly.
2 No, it goes in only one direction round the loop.
3 No, only one device may send data at any given moment.
4 From the content of the message.
5 It cancels its own transmission.
 Task 12 Which of the network configurations on page 71 does this flowchart refer to?
Task 12 Which of the network configurations on page 71 does this flowchart refer to?

 Task 13 The columns below describe characteristics of the bus and ring configurations.
Task 13 The columns below describe characteristics of the bus and ring configurations.
Which column refers to which configuration? How did you decide?
A
varied time response calculable time response
easy expansion difficult reconfiguration
fault-tolerant fault-intolerant
simple more complex
Speaking
 |
| Task 14 | Work in pairs, A and B,using the information in the advertisement opposite. Prepare the role-play in advance and try not to refer to the advertisement during the activity. |
 Student A: You are a customer interested in the Netplan Eazy Kit. Before deciding whether to buy it, ask questions to find out:
Student A: You are a customer interested in the Netplan Eazy Kit. Before deciding whether to buy it, ask questions to find out:
1 what you need in order to use the Netplan Eazy Kit.
2 the total number of PCs you can run on it.
3 the cost of adding additional PCs.
4 how difficult it is to install.
5 what software it runs.
6 the other features offered.
Student B: You represent the makers of the Netplan Eazy Kit. Make notes about the features of the product. Answer any questions and try to encourage the customer to buy it.
| Netplan Eazy Kit from as little as £215 | |||

| |||
| This is not the only way to share software. If your idea of sharing software is looking over a colleague's shoulder, then Netplan may have the ideal solution. To benefit from a network you only need two PCs. The Netplan Eazy Kit costs just £215 and gives you all the hardware, software, and cabling you need to link two PCs. And for £100 per PC you can extend the network to up to six users. With Netplan Eazy even the smallest business can save time, money, and effort. | |||
| Extra efficiency The Netplan Eazy Kit allows PCs to share the same data and software without having to copy and transfer disks. So whether you're dealing with customer enquiries or updating accounts, you can do it from the same machine. You can even send messages from one PC to another by e-mail. Netplan Eazy will also save you money on expensive resources like printers. | It's so Eazy If you can use a screwdriver, you can install Netplan Eazy yourself. That's all it takes. And once installed, it runs on all popular software. We also offer our customers unlimited access to our Freephone Helpline as part of the package. So why wait? Contact your nearest Netplan dealer today. Details are on the back cover of this magazine. | ||
 Word-play
Word-play
Task 15 Solve the crossword puzzle using the clues below.
Across
1 The means of communication between a human and a computer. (4,9)
5 To load software on to a computer, ready for use. (7)
7 To transmit a message to all nodes on a network. (9)
9 and 3 down Usually found in one building or a group of buildings close together. (5,4, 7)
10 This kind of network often uses a telephone exchange to connect different devices directly. (8)
Down
2 Taking place at exactly the same time as something else. (11)
3 See 9 across.
4 An_____ board may be inserted into a computer to give it added features. (9)
6 The opposite of 9 across and 3 down. (3)
8 The network configuration in which all devices are linked through the central computer. (4)
Language focus
Time sequence
In activities such as scheduling, doing routine activities, and conducting and describing experiments, it is important to recognize the sequence of events. As we know, events do not simply occur in isolation, they occur either before, during, or after other events. This time sequence may be chronological, logical, or causal. The following tables show examples of time relaters.
1 Before given time-references:
 Time relaters
Time relaters
 |
| Adjectives Adverbials | earlier former already prior before before that before then | preceding previous earlier first formerly originally up to now/then until now/then | previously so far yet in the beginning (long) ago |
Examples:
1 The memory storage capacity of earlier computers was not as large as those of today.
2 When the first digital computer was developed, the first analog computer had already been in use for some time.
3 Up to now, voice recognition technology has not been developed for mass marketing.
2 Simultaneous with given time-references:

 Time relaters
Time relaters
|
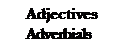
 at present
at present
at this point now/then
today
for the time being at the moment
at that time
meantime meanwhile
in the meantime when
at the same time


 Examples:
Examples:
1 At that time many new computer programs were being developed for use in businesses.
2 Computers may soon take over many daily tasks, but in the meantime ordinary people must continue to do them themselves.
3 Computer magazines keep us informed about contemporary issues in the computing world.
| 3 After given time-references: | |||
| Adjectives Adverbials | Time relaters | ||
| following afterwards after that eventually | later since by the time | next by the end soon next | |
| Examples: |
1 Since the development of the chip, computers have become cheaper and more compact.
2 You should have a good idea of the various applications of computer software by the time you finish reading this book.
3 Although initial versions of word-processing programs were not very complex, later versions were much more sophisticated.
Sample paragraph:
Computers, as we know them today, have not been around for a long time. It was not until the mid-1940s that the first working digital computer was completed. But since then, computers have evolved tremendously. Vacuum tubes were used in the first-generation computers only to be replaced by transistors in the second-generation computers at the beginning of the early1960s. By the end of the 1960s, transistors themselves were replaced by tiny integrated circuit boards and, consequently, a new generation of computers was on the market. Fourth-generation computers are now produced with circuits that are much smaller than before and can fit on a single chip. Even now, new technologies are being developed to make even better machines.
| Exercise 1 | Read the following paragraph and, as you read, underline the time relaters. During the seventeenth and eighteenth centuries, many easy ways of calculating were devised. Logarithm tables, calculus, and the basis for the modern slide rule were invented during this period. It was not until the early 1800s that the first calculating machine appeared and, not too long after, Charles Babbage designed a machine which became the basis for building today's computers. A hundred years later, the first analog computer was built, but the first digital computer was not completed until 1944. Since then, computers have gone through four generations: digital computers using vacuum tubes in the 1950s, transistors in the early 1960s, integrated circuits in the mid-60s, and a single chip in the 1970s. In the 1980s, we saw computers become smaller, faster, and cheaper. Earlier this decade, computers became portable, from laptops to palmtops. At the rate computer technology is growing now, we can expect further dramatic developments before the end of the century. |
 Read the following sentences which come from previous units. Underline the time relaters and indicate whether they refer to before, during, or after the given time reference. The first one has been done for you.
Read the following sentences which come from previous units. Underline the time relaters and indicate whether they refer to before, during, or after the given time reference. The first one has been done for you.
1 after Since then, over seventy million PCs made by IBM and other
manufacturers have been sold. (Unit 1)
2 Over this period, PCs have become commodity items. Since IBM
made the design non-proprietary, anyone can make them. (Unit 1)
3 _ Ten years later, in 1991, IBM were making PCs with 16Mb of
memory, expandable to 64Mb, running with a processor speed of 33MHz.
(Unit 1)
4 Large companies are considering running major applications on PCs, something which, ten years ago, no one would have believed possible of a PC. (Unit 1)
5 ____________ When the computer finds the closest match, it encodes the
character in memory and displays it on the screen as if it has been typed.
(Unit 2)
6 Enter the clipboard computer, a technology that has been in development for the last 20 years but took hold in the mass market only this year. (Unit 2)
7 Eventually, we're all going to be interlinked, no matter which
service we use, in what DIALOG's Richard Ream calls a 'network of networks'. (Unit 3)
8 Until then, most of us have to go to more than one service to
find everything we need. (Unit 3)

| Exercise 3 | Now refer back to paragraphs 1, 2, 4, and 5 of the text entitled Computer networks (page 67, Unit 6). Underline all the time relaters and indicate whether they refer to before, during, or after the given time reference. |


Start-up
Task 1 Try to answer these questions.
1 What is a computer virus?
2 How does a virus work?
Reading
Task 2 Before reading the text, match the words and definitions listed below.
1 a detonator
2 an infector
3 to boot
4 to trigger
5 to erase
6 pirated
7 a shield
8 to detect
a a protective device
 b to remove all traces of something
b to remove all traces of something
c a device used to set off an explosion or other destructive process
d to discover or recognize that something is present
e to set a process in motion
f something which transmits a disease or virus
g stolen, obtained without the owner's consent
h to load the operating system into memory
 Task 3 Now read the text to check your answers to Task 1.
Task 3 Now read the text to check your answers to Task 1.
How computer viruses work
| A |
computer virus — an unwanted program that has entered your system without you knowing about
5 it— has two parts, which I'll
call the infector and the
detonator. They have two
very different jobs. One of
the features of a computer
10 virus that separates it from other kinds of computer program is that it replicates itself, so that it can spread
(via floppies transported
15 from computer to computer, or networks) to other computers.
After the infector has
copied the virus elsewhere,
20 the detonator performs the virus's main work. Generally, that work is either damaging data on your disks, altering what you see on your
25 computer display, or doing something else that interferes with the normal use of your computer.
Here's an example of a
30 simple virus, the Lehigh virus. The infector portion of Lehigh replicates by attaching a copy of itself to COMMAND.COM (an
35 important part of DOS), enlarging it by about 1000 bytes.
So let's say you put a floppy containing
40 COMMAND.COM into an infected PC at your office —that is, a PC that is running the Lehigh program. The infector portion of Lehigh
45 looks over DOS's shoulder, monitoring all floppy accesses. The first time you tell the infected PC to access your floppy drive, the Lehigh
50 infector notices the copy of
COMMAND.COM on the
floppy and adds a copy of
itself to that file.
Then you take the floppy 105
55 home to your PC and boot
from the floppy. (In this case, you've got to boot from the
floppy in order for the virus
to take effect, since you may
so have many copies of COMMAND.COM on your
hard and floppy disks, but
DOS only uses the COMMAND.COM on the 115
65 boot drive.)
Now the virus has silently
and instantly been installed
in your PC's memory. Every
time you access a hard disk 120
70 subdirectory or a floppy disk containing COMMAND.COM, the virus sees that file and
infects it, in the hope that this particular COMMAND.COM 125
75 will be used on a boot disk on
some computer someday.
Meanwhile, Lehigh keeps a count of infections. Once it
has infected four copies of 130
80 COMMAND.COM, the
detonator is triggered. The detonator in Lehigh is a
simple one. It erases a vital
part of your hard disk, 135
85 making the files on that part
of the disk no longer
accessible. You grumble and set about rebuilding your
work, unaware that Lehigh is 140 90 waiting to infect other unsuspecting computers if
you boot from one of those
four infected floppies.
Don't worry too much 145
95 about viruses. You may
never see one. There are just a few ways to become
infected that you should be
aware of. The sources seem 150
100 to be service people, pirated games, putting floppies in
publicly available PCs
without write-protect tabs, commercial software (rarely), and software distributed over computer bulletin board systems (also quite rarely,
despite media misinformation).
Many viruses have spread through pirated — illegally copied or broken — games. This is easy to avoid. Pay for your games, fair and square.
If you use a shared PC or a PC that has public access, such as one in a college PC lab or a library, be very careful about putting
floppies into that PC's drives without a write-protect tab. Carry a virus-checking
program and scan the PC before letting it write data onto floppies.
Despite the low incidence of actual viruses, it can't hurt to run a virus checking
program now and then. There are actually two kinds of antivirus programs: virus shields, which detect viruses as they are infecting your PC, and virus scanners, which detect viruses once they've infected you.
Viruses are something to worry about, but not a lot. A little common sense and the occasional virus scan will keep you virus-free.
Remember these four points: Viruses can't infect a data or text file.
Before running an antivirus program, be sure to cold-boot from a write-
protected floppy.
Don't boot from floppies except reliable DOS disks or your original production disks.
Stay away from pirated software.
 Vocabulary
Vocabulary
fair and square (1. 113) — honestly
it can't hurt (1. 126) — it's probably a good idea

 |
| Task 4 | Decide whether the following statements are true (T) or false (F) in relation to the information in the text. If you feel a statement is false, change it to make it true. 1 Viruses cannot be spread through a computer network, only via floppies transported from computer to computer. 2The virus will spread as soon as you put the infected floppy in your PC. 3The infector works by interfering in some way with the normal use of your computer. 4The detonator in Lehigh works by altering what you see on your screen. 5Most viruses spread through pirated games. 6You should run an antivirus program every time you use your computer. 7There are not very many viruses in circulation. 8 IVirus shields are more effective than virus scanners. |
 Task 5 Indicate the line reference where the following ideas are found in the text.
Task 5 Indicate the line reference where the following ideas are found in the text.
line
1 1. The Lehigh virus must infect four copies of COMMAND. COM before
damage is done to data.
2 1 _ _ Always boot your computer from dependable DOS disks or your original disk.
3 1. The infector part of a virus must first copy itself somewhere before the
detonator part damages the data on your disks.
4 1_ Virus scanners discover viruses after the infection and virus shields
discover viruses during the infection process.
 Task 6 These are answers to questions about the text. Write the questions.
Task 6 These are answers to questions about the text. Write the questions.
1 Two, one that infects and one that does the damage.
2 By interfering in some way with the normal use of the computer.
3 After it has infected four copies of COMMAND.COM.
4 Every time you access a hard disk subdirectory or a floppy disk containing COMMAND.COM.
5 Yes, by using your common sense and by occasionally scanning for them.

| Task 7 | Using the line reference given, look back in the text and find the reference for the words in italics. 1 They have two very (line 7) 2is that it replicates itself (line 12) 3enlarging it by about (line 36) 4of itself to that file (line 53) 5and infects it (line 73) 6 This is easy to (line 112) 7 which detect viruses (line 131) 8once they've infected (line 134) |
 |
| Task 8 | Using the line references given, look back in the text and find words or phrases with a similar meaning to: 1 reproduces (lines 10-15) 2 infect (lines 12-17) 3 changing (lines 20-25) 4 immediately (lines 65-70) 5 complain (lines 85-90) Using the line references given, look back in the text and find words or phrases that have an opposite meaning to: 6 reducing (lines 35-40) 7 removed from (lines 65-70) 8 records (lines 80-85) 9 ignorant (lines 9 5-100) 10 frequently (lines 100-105) |
Computer security
Security breach blamed on hacker'
Year-old
Hacks into
Bank's database
| Hacker causes chaos in city hospital |
 Computer fraud on the increase
Computer fraud on the increase
Speaking
 Task 9 In pairs, try to answer these questions:
Task 9 In pairs, try to answer these questions:
1 Who or what is a 'hacker'?
2 How many ways can you think of to make the data in a computer secure?
Listening
 Task 10 Listen to Steve, a computer technician, and Richard, the office manager at a
Task 10 Listen to Steve, a computer technician, and Richard, the office manager at a
language institute, talking about computer security.
As you listen to the conversation, answer the following questions.
1 What is the problem with the computer system at the language institute?
2 What would someone need to connect his/her PC to the office network?
3 What are the disadvantages of security passwords, according to Steve and Richard?
4 How does the 'smart' card work? Is it safe?
5 How much do you think Steve and Richard know about security systems?
 |
| Speaking | |
| Task 11 | Steve and Richard must decide what to do. What advice would you give them? In groups or pairs, note down the advantages and disadvantages of the possible solutions. Think about safety, cost, and ease of use. Try to decide on the best solution. |
Reading
| Task 12 | 
|
The combined threat of viruses y,reakii.g havoc on y ,ir PC and probing meddlers gaining access to sensitive dai can strike fear into the hearts of even the most mild-mannered PC managers. Relax XTree Company has the ultimate in PC protection. AllSafe teams superior vims prevention with aura, 0,11701 and security reporting.
And while most ant-virus produc_, simply scan or known virus signatures, AitSafe actually looks for the signs of viruses attempting to replicate. Once a virus is spotted, AllSafe isolates it, preventing the virus from infecting your PC. If the virus is known, AllSafe quickly removes it. Even it the virus is unknown, AllSafe studies it and learns its signature immediately, letting you automafically update the virus signature database Then you can use AllSale to scan other disks or
systems right away before
an infection can spread,
without waiting for a new AUSAFE
signature from the
are publisher. So, if you use a,gandalone PC, fear not Its over for the evil virus.
Just as scary as the viruses are those characters that attempt to invade your computer files without authorization. AllSafe's flexible password options let you share or limit acces to as much of your hard disk as you wish. AllSafe keeps out the evil invaders!
When you need a complete solution - protection against both viruses xi(' unauthorized entry - choose AllSafe. And like all XTree Company products, they're easy to install and use. For more information or to find out where you can buy AilSafe, call one of our distributors:
Softsel UK (081) 588-8866 P&P (0706)217-744
Ingram Micro UK (0908)260460 Frontline (0256)27890
XTREE
COMP
 qc 01191 LleMS■iteffe, ram
qc 01191 LleMS■iteffe, ram
FREE FACTS 091
The flowchart on the following page represents the steps in the process by which AliSafe removes viruses from PCs. Using the information in the advertisement, match each step with the corresponding letter in the flowchart.
1 Virus signature database is updated.
2 Is virus known?
3 AllSafe scans other disks or systems in order to prevent further infection immediately.
4 AllSafe searches for indications that viruses are
attempting to copy themselves.
5 AllSafe identifies and isolates the virus.
6 AllSafe eliminates the known virus.
7 AllSafe analyses the virus and learns its signature straight away.
 Task 13 Find words or phrases in the text which mean:
Task 13 Find words or phrases in the text which mean:
1 wickedness, badness, danger
2 hides (while waiting to attack)
3 causing a lot of damage
4 people who interfere without authorization
5 terrify, make very afraid
6 combines
7 identified, recognized
8 frightening
9 choices
10 attackers
Speaking
 Task 14 Discuss the following questions:
Task 14 Discuss the following questions:
1 What technique does the advertisement use to persuade people to buy the product?
2 Do you think the advertisement is successful? Give reasons for your opinion.
3 What other techniques could be used to sell this kind of software?
 |
| Task 15 Task 16 | Writing Design an advertisement for a PC protection package. Your advertisement should mention all the features listed below, but you may add others. Choose a name, and decide on the best way to present your product. Features Password protection — system manager controls what each user is permitted to do File encryption — plain text messages are converted into cipher (code) so that only authorized recipients can read them Keyboard lock — screen is cleared and keyboard is locked after pre-set period of inactivity Reading Read this news report and discuss the questions that follow. |
 NSA consultant's son is
NSA consultant's son is
Computer saboteur
`Worm' came from graduate student
 A A
|
court heard today how a Cornell University graduate student,
Robert T. Morris Jr. (25), infected a host of government and educational computer centres with a computer virus, known as a 'worm', which literally brought all computational activity to a halt in over 6,000 installations. Morris, the son of a prominent National Security Agency computer consultant, was sentenced for his offences yesterday. As punishment, he was required to spend no time in prison but, instead, serve three years' probation, contribute 400 hours of community service, and to pay a $10,000 fine along with associated court and probation costs.

 1 How serious do you think Robert Morris's crime was?
1 How serious do you think Robert Morris's crime was?
2 Do you think the punishment was
a too severe?
b about right?
c not severe enough?
3 Do you know of any similar incidents of computer hacking?
 Word-play
Word-play
 The words and phrases below are taken from this unit. In pairs or groups, decide if they have a 'protective' or a 'destructive' meaning as they are used in the unit, then put them under the correct heading.
The words and phrases below are taken from this unit. In pairs or groups, decide if they have a 'protective' or a 'destructive' meaning as they are used in the unit, then put them under the correct heading.
| detonator | infector | erase | pirated |
| infect | write-protect tab | worm | virus scanner |
| hacker | password | smart card | shield |
| signature protective | cipher destructive | keyboard lock | access control |












 How many other ways can you think of to classify them?
How many other ways can you think of to classify them?
 Language focus G
Language focus G
Listing
It is important when reading to recognize and understand the relationship in which sentences and groups of sentences combine to present information. This information may be linked by means of a connective word or marker.
Making a list, for example when enumerating, and giving instructions, indicates a cataloguing of what is being said. It is important to note that most enumerations belong to clearly defined sets. The following table is a list of the markers that can be used to show the order in which things are to be said.
1, 2, 3, etc.
one, two, three, etc.
first(ly), second(ly), third place
another, next, then
furthermore, afterwards, moreover
lastly/finally
to begin/start with, and to conclude
first and foremost} mark the beginning
first and most important(ly) of a descending order
above all mark the end of
last but not least an ascending order
There are many ways of showing sequential relationships. Those given in the table above are not the only ones, they are the most common ones used in listing or enumerating. The -ly forms are usually used when listing.
Sample paragraphs:
More and more police departments are now using sophisticated devices to help control the increasing crime rate. Some of these devices are: firstly, a computer terminal inside a police vehicle to answer an officer's questions, secondly, a computer-controlled display unit for displaying fingerprints, and thirdly, educational systems for police officers such as terminals, enabling them to verify changes in laws, rules, and regulations.
The computer memory of many law enforcement systems contains all kinds of information. First and foremost, it has data on stolen items such as cars, licence plates, and property. Second, it has information on missing persons and wanted fugitives. Last but not least, it contains information on political extremist groups and their activities.

 Computers have certainly revolutionized police work by providing access to millions of items of information with the least possible delay and speeding up the process of apprehending suspicious-looking characters.
Computers have certainly revolutionized police work by providing access to millions of items of information with the least possible delay and speeding up the process of apprehending suspicious-looking characters.
 l
l
Exercise 1 Complete the following paragraph about the various steps in the creation of a
database by filling in the blanks with appropriate listing markers.
| When you are creating a new database, you must many fields you will need in your database. 2 | decide how, you will have to |
provide up to five items of information about each field. ________, each
field needs to have a name. 4, the field type has to be defined.
Character, numeric, date, and logical are some common types. s
choice to be made is the width of the field. However, some fields, such as date,
| have present default values. The 6 decimal places if the field is numeric. 7 whether the field is to be indexed or not. | step is to set the number of , you will have to indicate | |
Exercise 2 Complete the following paragraph by filling in the blanks with appropriate
listing markers.
Computers can do wonders, but they can waste a lot of money unless careful consideration goes into buying them. Businessmen and women thinking of buying a computer system should I__________________________ admit they know very little
about computers. 2 ______________________________________________, they must realize that the computer sales
people don't always know how their business works.
, it is essential that buyers should get outside advice, not necessarily from consultants but from other executives who have had recent experience in buying a computer system 4 they should try to see
systems similar to ones under consideration in operation. Because their operations will have differences that must be accommodated, they should
_______ find out what would be involved in upgrading a system.
__________ important thing to know before buying a computer is the
financial situation of the supplier because computer companies come and go and not all are financially stable. ', the prospective buyer should
demand that every detail be covered in writing, including hardware and software if they are supplied by different companies. There's nothing wrong with computers themselves, it's how and why they are used that can cause problems.


 Computers in the office
Computers in the office
| Start-up What aspects of computer technology are illustrated below: Make a list of any other examples used in the office. | |
| Task 1 a |
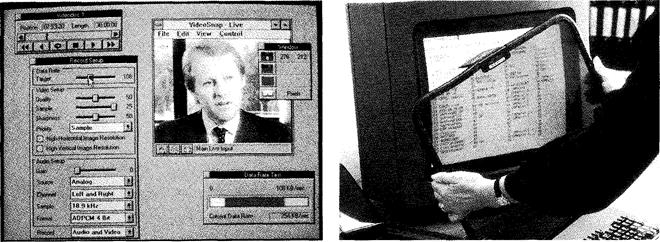
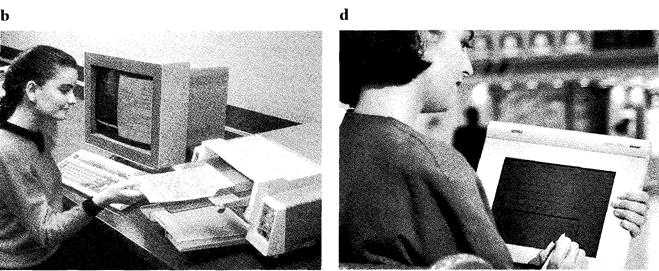
Reading
 Task 2 Read the text opposite. How many of the items you listed in Task 1 are
Task 2 Read the text opposite. How many of the items you listed in Task 1 are
mentioned:
Visions of Tomorrow
| F |






