–азработан в 1971 году и формализует матрицу доступа
ћ Ц матрица прав доступа
Q Ц текущее состо€нии системы
Q(S,O,M)
ћ(S,O) Ц €чейка матрицы, содержаща€ набор прав доступа субъекта S к объекту O
ѕоведение системы во времени моделируетс€ переходами между различными ее состо€ни€ми. ѕереходы осуществл€ютс€ путем внесени€ изменений в матрицу M с использованием команд следующего вида:
Command a(x1,xk)
if r1 in M[Xs1,Xo1] and
if r2 in M[Xs2,Xo2] and
Е
if rm in M[Xsm,Xom] and
then
op1
op2
Е
a Ц »м€ команды
xi Ц параметры команды, представл€ющие идентификаторы субъектов и объектов
opi Ц элементарные операции, которые будут выполнены в том случае, если выполн€ютс€ все без исключени€ услови€ из блока if Е then.
¬ результате выполнени€ операции команда переходит из состо€ни€ Q=(S,O,M) в состо€ние QТ=(SТ,OТ,MТ).
ћодель предусматривает наличие 6 элементарных операций
1) Enter r into M[s,o] (s*принадлежит*S,o*принадлежит*O)
ƒобавление к субъекту S права r по отношению к объекту O. ¬ результате выполнени€ команды происходит следующее изменение в состо€нии системы:
SТ=S
OТ=O
MТ[xs,xo]= M[xs,xo], если (xs,xo) не равно (s,o)
MТ[s,o]= MТ[s,o]v{r}
2) Delete r from M[s,o] (s*принадлежит*S,o*принадлежит*O)
”даление у субъекта S права r по отношению к объекту O
SТ=S
OТ=O
MТ[xs,xo]= M[xs,xo], если (xs,xo) не равно (s,o)
MТ[s,o]= MТ[s,o]\{r}
3) Create subject s (s#не принадлежит#S)
—оздание нового субъекта s
OТ=Ov{s}
SТ=S v{s}
MТ[xs,xo]= M[xs,xo] дл€ любых (xs,xo)#принадлежащих#S*O
MТ[s,xo]=#не пустое множество# дл€ любых xo#принадлежащих#OТ
MТ[s,xo]=#не пустое множество# дл€ любых xs#принадлежащих#SТ
4) Destroy subject s (s#принадлежит#S)
”даление существующего субъекта s
SТ=S\{s}
OТ=O\{s}
MТ[xs,xo]= M[xs,xo] дл€ любых (xs,xo)#принадлежащих#S*O
5) Create object o (o#не принадлежит#O)
OТ=Ov{o}
SТ=S
MТ[xs,xo]= M[xs,xo] дл€ любых (xs,xo)#принадлежащих#S*O
MТ[xs,o]=#не пустое множество# дл€ любых xs#принадлежащих#SТ
6) Destroy object o (o#принадлежит#O)
”даление существующего объекта o
OТ=O\{o}
SТ=S
MТ[xs,xo]= M[xs,xo] дл€ любых (xs,xo)#принадлежащих#SТ*OТ
ѕример
1. —оздание файла
command create_file (p,f)
create object f
enter own into M[p,f]
enter r into M[p,f]
enter w into M[p,f]
end
создает объект own, надел€ет пользовател€ правами чтени€ и записи.
2. —оздание процесса (процесс p создает процесс q и получает на него права чтени€, записи и владени€, передава€ процессу q права записи и чтени€ по отношению к самому себе)
command exec_process (p,q)
create subject q
enter own into M[p,q]
enter r into M[p,q]
enter w into M[p,q]
enter r into M[q,p]
enter w into M[q,p]
end
3. ѕередача права чтени€ по отношению к файлу. ѕраво чтени€ на файл f передаетс€ владельцем p субъекту q
command grand_read (p,q,f)
if own in M[p,f]
then
enter r into M[q,f]
end
‘ормальное описание системы в модели ’аррисона-–уззо-”льмана выгл€дит следующим образом
#—истема#=(Q,R,C)
—остоит из следующих элементов:
1) онечный набор прав доступа R={r1,Е,rn}
2) онечный набор исходных субъектов So={s1,Е,sn}
|
|
|
3) онечный набор исходных объектов Oo={o1,Е,on}
4) »сходна€ матрица доступа Mo
5) онечный набор команд C={ai(x1,Е,xk)}
ѕоведение системы во времени рассматриваетс€ как последовательность состо€ний {Qi}, каждое последующее состо€ние €вл€етс€ результатом применений некоторой команды к предыдущей.
Е „ЄтотамЕ
ѕокажем, €вл€етс€ ли заданна€ система с некоторым начальным состо€нием безопасной относительно того или иного права доступа дл€ частного случа€. —истема E=(Q,R,C)называетс€ монооперационной, если кажда€ команда ai#принадлежит#— выполн€ет один примитивный оператор
Th:
—уществует алгоритм, который провер€ет исходное состо€ние монооперационной системы безопасным дл€ данного права ј.
ƒоказательство:
ѕокажем, что число последовательностей команд системы, которые необходимо проверить, €вл€етс€ ограниченным. ¬ этом случае проверка безопасности системы сведетс€ к полному перебору всех последовательностей и к проверке конечного состо€ни€ каждой из них на отсутствие утечки права ј. Ќет необходимости рассматривать более одного оператора create, т.к. система €вл€етс€ монооперационной и одна команда не может одновременно создать объект или субъект и модифицировать его права доступа, поскольку путем замены параметров можно ограничитьс€ работой с последовательност€ми команд, которые оперируют над существующими объектами или субъектами. ≈динственна€ команда create будет необходима на случай, если в начальном состо€нии в системе не было ни одного субъекта.
ѕусть —1,—2,Е,—n Ц последовательность команд, в результате выполнени€ которой происходит утечка права ј. ”простим эту последовательность команд следующим образом:
1) ”далим все команды Delete и Destroy.
2) ƒобавим в начало последовательности —1,—2,Е,—n команду Sinit следующего вида: create subject.
3) ѕроход€ последовательность команд справа налево, последовательно удалим все команды вида create subject, замен€€ ссылки на создаваемые с помощью этих команд объекты ссылками на Sinit.
4) јналогично удалим все команды вида create object, замен€€ на Sinit.
5) ”далим все команды вида enter, внос€щие право ј в €чейку, котора€ уже содержит это право.
ѕолучивша€с€ в результате данных преобразований последовательность команд также приводит к утечке права ј. ѕроанализируем состав возможных команд получившейс€ последовательности. оманды вида create object, destroy subject, destroy object и delete в ней отсутствуют. оманда create subject присутствует в единственном числе. ћаксимальное число команд вида enter равно |R|(|S0|+1)(|O0|+1), а общее число возможных команд равно |R|(|S0|+1)(|O0|+1)+1, а значит количество последовательностей команд ограничено, что и требовалось доказать.
сожалению расширить подобный результат на произвольные системы невозможно.
Th:
ƒл€ систем общего вида задача определени€ того, €вл€етс€ ли исходное состо€ние системы безопасным дл€ данного права ј, €вл€етс€ вычислительно неразрешимой. ƒл€ доказательства достаточно свести задачу проверки безопасности системы к заведомо неразрешимой задаче остановки машины тьюринга.
ћодель Ѕелла-Ћа ѕадулле
¬ модели Ѕелла-Ћа ѕадулле по грифам секретности распредел€ютс€ субъекты и объекты, действующие в системе и при этом выполн€ютс€ следующие правила:
1) ѕростое правило безопасности, Simple Security (SS) Ц —убъект с уровнем секретности Xs может читать информацию из объекта с уровнем секретности X0 тогда и только тогда, когда Xs преобладает над X0; Ђno read upї
|
|
|
2) * - свойство (property) Ц субъект с уровнем секретности Xs может писать информацию в объект с уровнем секретности X0 тогда и только тогда, когда X0 преобладает над Xs. Ђno write downї
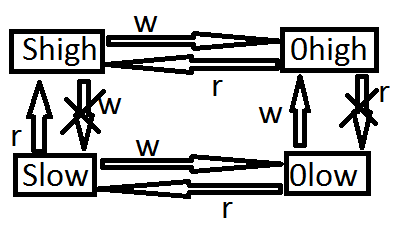
S#принадлежит#O
R={r,w}
L={u,su,s,ts} (unclassified, sensitive but unclassified, secret, top secret)
#дельта# - решетка уровн€ секретности.
V Ц множество состо€ний системы, представл€емое в виде набора упор€доченных пар (F,M)
F: SvO->L, где F Ц функци€ уровн€ секретности, став€ща€ каждому объекту и субъекту в системе в соответствие определенный уровень секретности.
M = матрица текущих прав доступа
#дельта# (L, <=,#жирна€ точка#,#крестик в кружочке#)
<= - оператор, определ€ющий частичное нестрогое отношение пор€дка дл€ уровней секретности
#жирна€ точка# - оператор наименьшей верхней границы
#крестик в кружочке# - оператор наибольшей нижней границы
ќтношение, имеющее <=, обладает следующими свойствами:
1) –ефлексивность (#дл€ любых# а #принадлежит# L:а <= а)
–азрешена передача информации между субъектами и объектами одного уровн€ секретности.
2) јнтисимметричность
(#дл€ любых# а1,a2 #принадлежит# L:((а1 <= а2)&(a2<=a1))->a2=a1)
¬ данном случае это означает, что информаци€ может передаватьс€ как от субъектов и объектов уровн€ ј к субъектам и объектам уровн€ ¬, так и от субъектов и объектов уровн€ ¬ к субъектам и объектам уровн€ ј, в таком случае эти уровне эквивалентны.
3) “ранзитивность
(#дл€ любых# а1,a2,a3 #принадлежит# L: ((а1 <= а2)&(a2<=a3))->a1<=a3)
“ранзитивность означает, что если информаци€ может передаватьс€ от субъектов и объектов уровн€ ј к субъектам и объектам уровн€ ¬, а от субъектов и объектов уровн€ ¬ к субъектам и объектам уровн€ —, то информаци€ также может передаватьс€ от субъектов и объектов уровн€ ј к субъектам и объектам уровн€ —.
ќператоры наибольшей нижней #крестик в кружочке# и наименьшей верхней #жирна€ точка# границы определ€ютс€ следующим образом:
а=а1#жирна€ точка#a2<=>(а1,a2<=a)&(#любой#aТ#принадлежит#L:(aТ<=a)->(aТ<=a1VaТ<=a2))
а=а1#крестик в кружочке#a2 <=> <=>(a<=а1,a2)&(#любой#aТ#принадлежит#L:(aТ<=a1)&(aТ<=a2)->(aТ<=a))
ƒл€ каждой пары существует единственный элемент наименьшей верхней границы и единственный элемент наибольшей нижней границы.
—истема ∑=(V0,R,T) в данной модели состоит из следующих элементов:
V0 Ц начальное состо€ние системы
R Ц множество прав доступа
T:VxR->V Ц функци€ перехода, котора€ в ходе выполнени€ запросов переводит систему из одного состо€ни€ в другое
»зменение состо€ни€ системы происходит следующим образом:
—истема, наход€ща€с€ в состо€нии v#принадлежит#V, получает запрос на доступ r#принадлежит#R и переходит в состо€ние V*=T(v,r). —осто€ние Vn называетс€ достижимым дл€ системы ∑, если существует последовательность:
{(Z0,V0),Е,(Zn-1,Vn-1),(Zn,Vn)}:T(Zi,Vi)=Vi+1,#любой#i=0,n-1
Ќачальное состо€ние V0 €вл€етс€ достижимым по определению.
—осто€ние системы (F,M) называетс€ безопасным по чтению или Simple-безопасным, если дл€ каждого субъекта, осуществл€ющего в этом состо€нии доступ по чтению к объекту, уровень безопасности субъекта доминирует над уровнем безопасности объекта.
#любой#s#принадлежит#S, #любой#o#принадлежит#O,
z#принадлежит#M[s,o]->F(o)<=F(s)
#любой#s#принадлежит#S, #любой#o#принадлежит#O,
w#принадлежит#M[s,o]->F(s)<=F(o)
—осто€ние (F,M) называетс€ безопасным по записи в случае, если дл€ каждого субъекта, осуществл€ющего в этом состо€нии доступ по записи к объекту, уровень безопасности объекта доминирует над уровнем безопасности субъекта.
—осто€ние (F,M) называетс€ безопасным, если оно безопасно по чтению и по записи. ѕолностью система ∑=(V0,R,T) называетс€ безопасной, если ее начальное состо€ние V0 безопасно и все состо€ни€, достижимые из V0 путем применени€ конечной последовательности запросов из R безопасны.
|
|
|
ќсновна€ теорема безопасности Ѕеллы-Ћа ѕадулле
—истема ∑=(V0,R,T) безопасна тогда и только тогда, когда выполнены следующие услови€:
1) Ќачальное состо€ние V0 безопасно
2) ƒл€ любого состо€ни€ V, достижимого из V0, путем применени€ конечной последовательности запросов из R таких, что
T(v,z)=V*
v=(F,M)
V*=(F*,M)
дл€ #любой#s#принадлежит#S,
#любой#o#принадлежит#O
¬ыполнены услови€:
a. If z#принадлежит#M*[s,o] и z#не принадлжит#M[s,o] then F*(o)<=F*(s)
b. If z#принадлежит#M[s,o] и F*(s)< F*(o), then z#не принадлжит#M*[s,o]
c. If w#принадлежит#M*[s,o] и w#не принадлжит#M[s,o] then F*(s)<=F*(o)
d. If w#принадлежит#M[s,o] и F*(o)< F*(s), then w#не принадлжит#M*[s,o]
ѕусть система ∑=(V0,R,T) безопасна.
V0 безопасно по определению
ѕредположим, что существует такое безопасное состо€ние V*, достижимое из состо€ни€ V:T(v,r)=V*
ƒопустим, дл€ данного состо€ни€ нарушено одно из условий (a-d), во всех случа€х мы получаем противоречи€ с тем, что состо€ние V* €вл€етс€ безопасным. ѕокажем достаточность утверждени€.
—истема ∑=(V0,R,T) может быть небезопасна в двух случа€х:
1) ¬ случае, если изначальное состо€ние V0 небезопасно (противоречит условию теоремы).
2) ¬ случае, если существует небезопасное состо€ние V*, достижимое из безопасного V0 путем применени€ конечного числа запросов из R. Ёто означает, что на каком-то этапе произошел переход “(v,r)=V*, где v Ц безопасное состо€ние, а V* - небезопасное, однако услови€ (a-d) делают данный переход невозможным.
„“ƒ
‘ормальные модели целостности
ћодель ларка-¬илсона (1987)
S Ц множество субъектов
D Ц множество данных в ј—
CDI (constrained data items) Ц данные, целостность которых контролируетс€
UDI (un constrained data items) Ц данные, целостность которых не контролируетс€
D=CDI#чашка (cup)#UDI
CDI#шапка (hat)#UDI=#пустое множество#
TP (transformation procedure) компонент, способный инициировать транзакцию
“ранзакци€ Ц последовательность действий, перевод€ща€ систему из одного состо€ни€ в другое
IVP (integrity verification procedure) Ц процедура проверки целостности CDI
ѕравила модели ларка-¬илсона:
1) ¬ системе должны иметьс€ IVP, способные подтвердить целостность любого CDI
2) ѕрименение любой TP к любому CDI должно сохранить целостность этого CDI
3) “олько TP могут вносить изменени€ в CDI
4) —убъекты могут инициировать только определенные TP над определенными CDI (система должна поддерживать отношени€ вида (s,t,d), где s,t,d соответственно принадлежат S,TP,CDI)
5) ƒолжна быть обеспечена политика разделени€ об€занностей субъектов, то есть субъекты не должны измен€ть CDI без вовлечени€ в операцию других субъектов системы
6) —пециальные TP могут превращать UDI в CDI
7) аждое применение TP должно регистрироватьс€ в специальном CDI, при этом:
a. ƒанный CDI должен быть доступен только дл€ добавлени€ информации
b. ¬ данный CDI необходимо записывать информацию, достаточную дл€ восстановлени€ полной картины функционировани€ системы
8) —истема должна распознавать субъекты, пытающиес€ инициировать TP
9) —истема должна разрешать производить изменени€ в списках авторизации только специальным субъектам
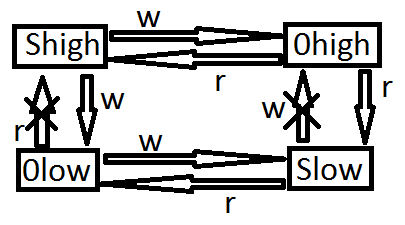
ћодель Ѕиба (1977)
ћодификаци€ Ѕеллы-Ћа ѕадулле дл€ целостности данных.
#дельта#=(IC, <=, #жирна€ точка#, #крестик в кружочке#) решетка классов целостности
IC Ц лассы целостности данных
Ѕазовые правила модели Ѕиба:
1) ѕростое правило целостности (Simple integrity, SI) Ц субъект с уровнем целостности Xs может читать информацию из субъекта с уровнем целостности X0 тогда и только тогда, когда X0 преобладает над Xs (No read down)
|
|
|
2) * - свойство (integrity) Ц субъект с уровнем целостности Xs может писать информацию в объект с уровнем целостности X0 тогда и только тогда, когда Xs преобладает над X0 (No write up)
ƒиаграмма информационных потоков
¬ большинстве приложений целостность данных рассматриваетс€ как некое свойство, которое либо сохран€етс€, либо не сохран€етс€ и введение иерархических уровней целостности может представл€тьс€ излишним. ¬ действительности же уровни целостности в модели Ѕиба стоит рассматривать как уровни достоверности, а соответствующие информационные потоки как передачу информации из более достоверной совокупности данных в менее достоверную и наоборот. ‘ормальное описание модели Ѕиба полностью аналогично описанию модели Ѕелла-Ћа ѕудуллы. достоинствам данной модели следует отнести ее простоту, а так же использование хорошо изученного мат. аппарата, недостатки аналогичны модели Ѕелла-Ћа ѕадуллы.






